Cybersecurity analysts have found a brand new phishing marketing campaign concentrating on crypto customers by deploying FatalRAT alongside the Clipper and Keylogger malware.
Cyble Analysis and Intelligence Labs have found a brand new phishing marketing campaign concentrating on Chinese language crypto traders and organizations, with an emphasis on customers of the Exodus crypto pockets.
In a weblog article, the cybersecurity consultants revealed that unidentified risk actors have used a pretend web site designed to imitate the interface of the Exodus crypto pockets in an try and trick victims into sharing their personal information with out realizing it.
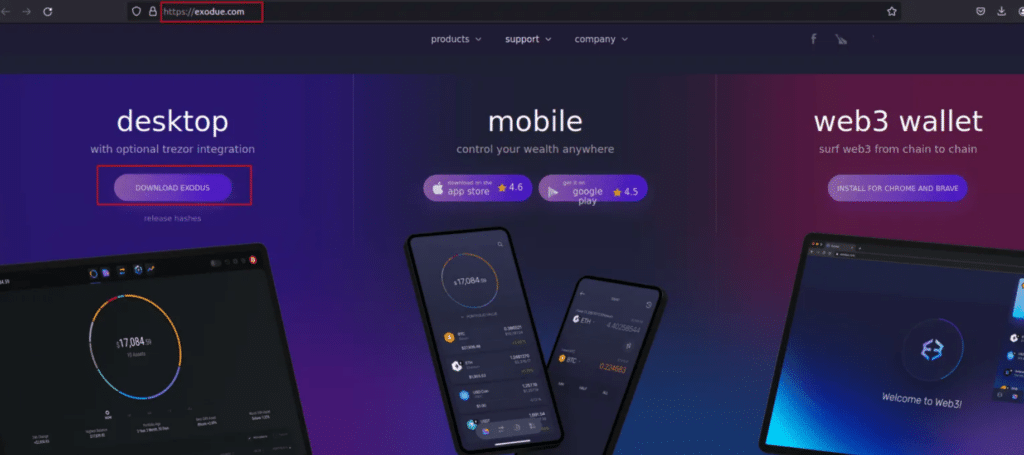
As soon as unsuspecting customers are tricked into downloading the software program, disguised as real Exodus installers, from the phishing website, they inadvertently set up FatalRAT, a kind of malware that hackers use to remotely take management of somebody’s pc. Moreover, this system lures customers into launching the Exodus set up, making them suppose it’s actual, whereas in truth diverting their consideration to cover its true intentions.
Cyble notes that along with the Exodus program, the installer additionally deploys different malicious parts resembling Clipper and Keylogger, applications designed to intercept and modify clipboard information on a sufferer’s pc. The analysts highlighted that this time the hackers have used new .dll side-loading methods as a part of their technique to evade detection. Whereas it isn’t clear how massive the assault is, the hackers look like concentrating on Chinese language crypto traders and corporations with Chinese language-language installers, Cyble famous.

